Add External User as a Guest in Azure AD
Access Microsoft Entra Admin Center
Go to the Microsoft Entra admin center: https://entra.microsoft.com
Fill Out the Form
Complete the invitation form:
- Display Name: Full name of the user
- Email: External email address (e.g., Gmail, or another company domain)
- You may optionally personalize the invitation message
Assign Guest User to the Neo Agent App
Access Enterprise Applications
In the Entra Admin Center, go to: Applications > Enterprise applications
Find Neo Agent App
Search for Neo Agent, and click into the app
- Application ID:
3da03a86-b850-4c07-96e5-7590022efe11
Assign Role (Optional)
If you’ve defined App Roles in your Neo Agent App Registration (e.g., Viewer, Admin), assign the appropriate role here
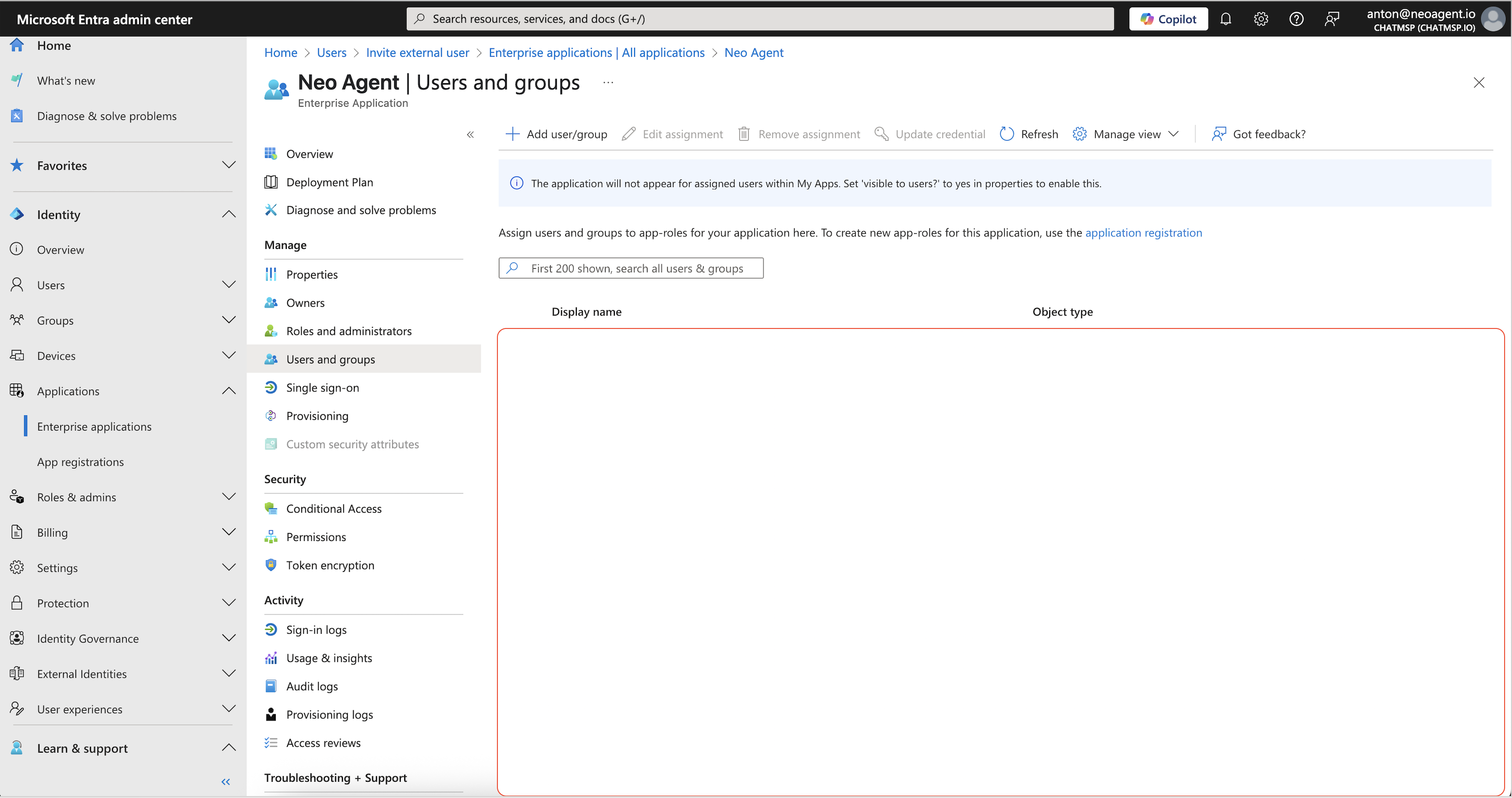
Restrict Access to Everything Else (Optional but Recommended)
When you invite a guest user (external user) into your Microsoft Entra ID tenant, they have zero access by default to your resources. To ensure the guest user only accesses Neo Agent:- Do not assign them to any other Azure groups or roles
- Avoid assigning any Azure roles like Contributor or Reader
Let the Guest User Log In
The guest user will receive an invite email from Microsoft. Once accepted, they can:- Sign in to the Neo Agent web app via your standard login URL: https://dashboard.neoagent.io
- Use Microsoft OAuth just like your internal users
Troubleshooting Access Issues
If they encounter an “Access Denied” error:- Verify they accepted the invite
- Check that they are assigned to the Neo Agent enterprise app
- Review Conditional Access policies that may block them
Frequently Asked Questions
Can I use a Gmail or Outlook address for the guest user?
Can I use a Gmail or Outlook address for the guest user?
Yes. Microsoft Entra supports any email via its B2B system. If the user doesn’t have a Microsoft account, they’ll be prompted to create one during the invitation acceptance process.
Can I revoke access later?
Can I revoke access later?
Yes. You can:
- Remove them from the Neo Agent application assignment
- Delete the user entirely from your directory if needed
- Disable their account temporarily if you need to suspend access
Will the external user see our other Microsoft services?
Will the external user see our other Microsoft services?
No. Guest users only have access to resources you explicitly assign to them. By default, they cannot see or access any other services, applications, or data in your tenant.
How do I manage multiple external users?
How do I manage multiple external users?
You can create Azure AD groups specifically for external Neo Agent users and assign the entire group to the Neo Agent application. This makes management easier when you have multiple contractors or partners.
Can external users access Neo Agent's RBAC features?
Can external users access Neo Agent's RBAC features?
External users will be subject to the same RBAC permissions within Neo Agent as internal users. You can assign them appropriate roles (Admin, User, Viewer) based on their needs and responsibilities.
Security Best Practices
- Regular Review: Periodically review all external user accounts and remove those no longer needed
- Time-Limited Access: Consider setting expiration dates for external user accounts when possible
- Monitor Activity: Use Azure AD audit logs to monitor external user activity
- Conditional Access: Apply appropriate Conditional Access policies to external users based on your security requirements
- Documentation: Maintain records of why each external user was granted access and when their access should be reviewed
External user access is managed entirely through Microsoft Entra ID. Neo Agent inherits the authentication and authorization decisions made by your identity provider, ensuring consistent security policies across all your applications.
